本课程全面概述了 Google Cloud Security Command Center (SCC) Enterprise,这是一个云原生应用保护平台 (CNAPP) 解决方案,可帮助组织预防、检测和应对整个 Google Cloud 服务中的威胁。 您将了解 SCC Enterprise 的核心功能,包括增强型威胁检测、深度漏洞管理和集成式案例管理。 本课程也会介绍威胁管理和漏洞评估方面的基本概念,并实际演示如何使用 SCC Enterprise 来识别、调查和修复多云环境中的安全风险。

本课程全面概述了 Google Cloud Security Command Center (SCC) Enterprise,这是一个云原生应用保护平台 (CNAPP) 解决方案,可帮助组织预防、检测和应对整个 Google Cloud 服务中的威胁。 您将了解 SCC Enterprise 的核心功能,包括增强型威胁检测、深度漏洞管理和集成式案例管理。 本课程也会介绍威胁管理和漏洞评估方面的基本概念,并实际演示如何使用 SCC Enterprise 来识别、调查和修复多云环境中的安全风险。
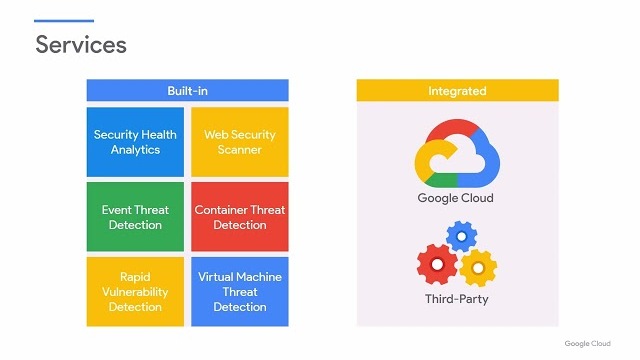
Learn about the fundamental features of Security Command Center on Google Cloud. Spend time in this course to understand assets, detection and compliance. Security Command Center is a key part of your Google Cloud security journey, complete these modules and...

Complete the intermediate Mitigate Threats and Vulnerabilities with Security Command Center skill badge to demonstrate skills in the following: preventing and managing environment threats, identifying and mitigating application vulnerabilities, and responding to security anomalies.
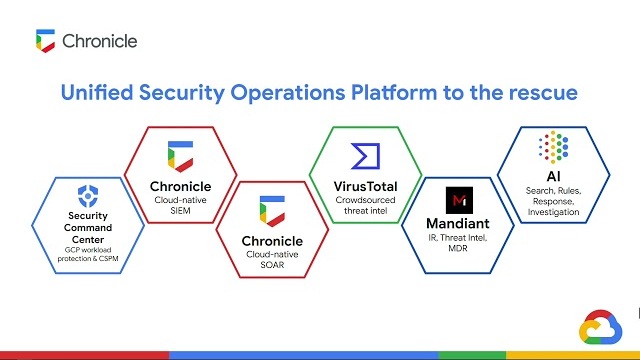
This course covers the basline skills needed for the Chronicle Security Operations Platform. The modules will cover specific actions and features that security engineers should become familiar with to start using the toolset.

This course reviews the essential security features of Model Armor and equips you to work with the service. You’ll learn about the security risks associated with LLMs and how Model Armor protects your AI applications.

Modern Security Operations, based on Google's Autonomic Security Operations framework and Continuous Detection, Continuous Response (CD/CR) methodology is a combination of philosophies, practices, and tools that improve an organization's ability to withstand security attacks through an adaptive, agile, and highly...
Aanalyze a false positive threat using the Security Command Center (SCC) and take action to address it.

In this lab, you test your Security Command Center skills by demonstrating your proficiency in creating mute rules, analyzing and fixing high vulnerability findings, identifying application vulnerabilities, and exporting Findings.